Modeling File Behavior
- 19 Apr 2023
- 1 Minute to read
-
Print
-
DarkLight
Modeling File Behavior
- Updated on 19 Apr 2023
- 1 Minute to read
-
Print
-
DarkLight
Article Summary
Share feedback
Thanks for sharing your feedback!
Overview
File Indicators can model a special Indicator-to-Indicator association, which is based on their behavior once opened. These associations can be used to model the fact that malware may contain and create additional files or communicate with network devices. This behavior can be modeled on a File Indicator’s Details screen.
Before You Start
| Minimum Role(s) |
|
|---|---|
| Prerequisites | A File Indicator |
Viewing a File Indicator’s Behavior Model
- Navigate to the legacy Details screen for a File Indicator.
- Click the Behavior tab. The Behavior screen will be displayed (Figure 1).
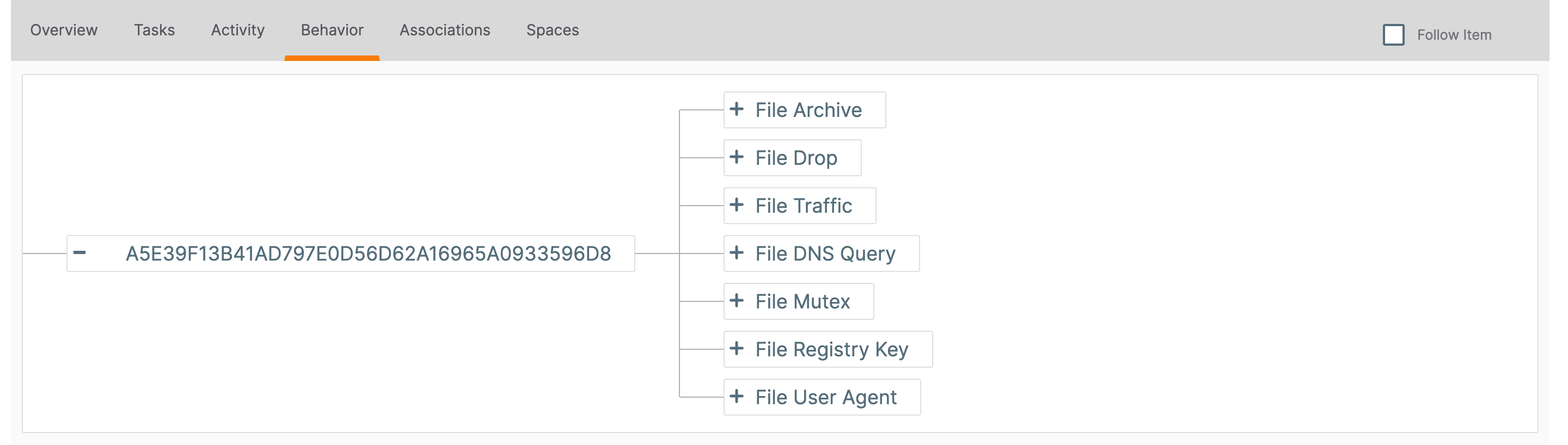
Modeling Behavior
File behavior is represented as a tree, with each branch consisting of one of seven Indicator types:
- File Archive: This File Indicator contains other File Indicators.
- File Drop: This File Indicator creates another File Indicator.
- File Traffic: This File Indicator communicates with a Host, Address, or URL Indicator.
- File DNS Query: This File Indicator attempts to retrieve the DNS record for a Host Indicator.
- File Mutex: This File Indicator creates a Mutex Indicator.
- File Registry Key: This File Indicator creates a Registry Key Indicator.
- File User Agent: This File Indicator creates a User Agent Indicator.
Creating an Association
- Click Add
 to the left of a branch name (Figure 1). A New… button will be displayed to the right of the selected branch (Figure 2).
to the left of a branch name (Figure 1). A New… button will be displayed to the right of the selected branch (Figure 2).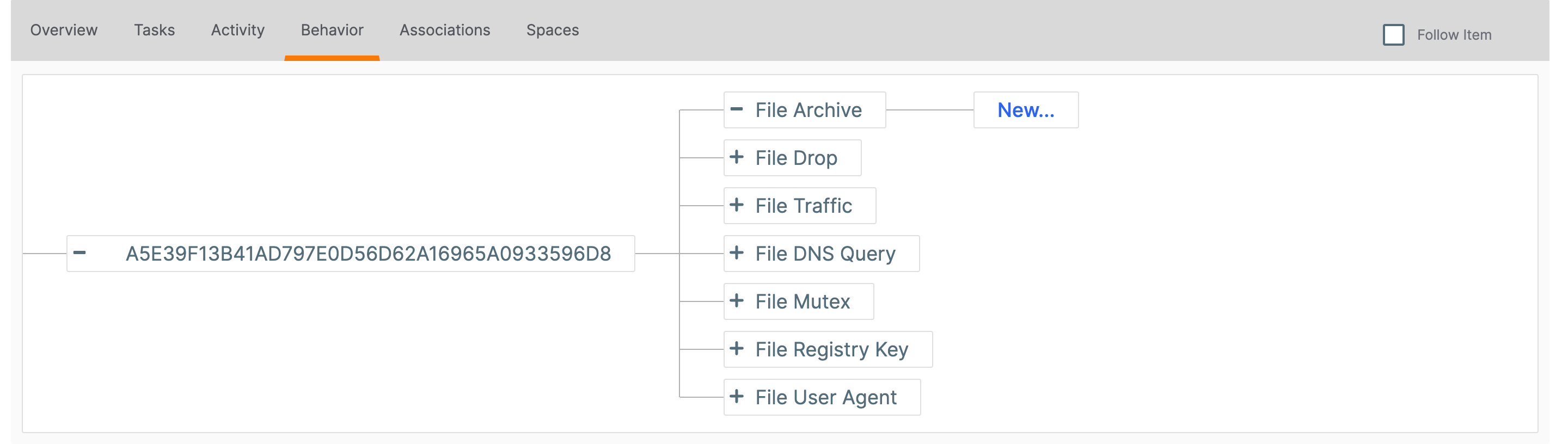
- Click the New… button. The Select an Indicator window will be displayed (Figure 3).
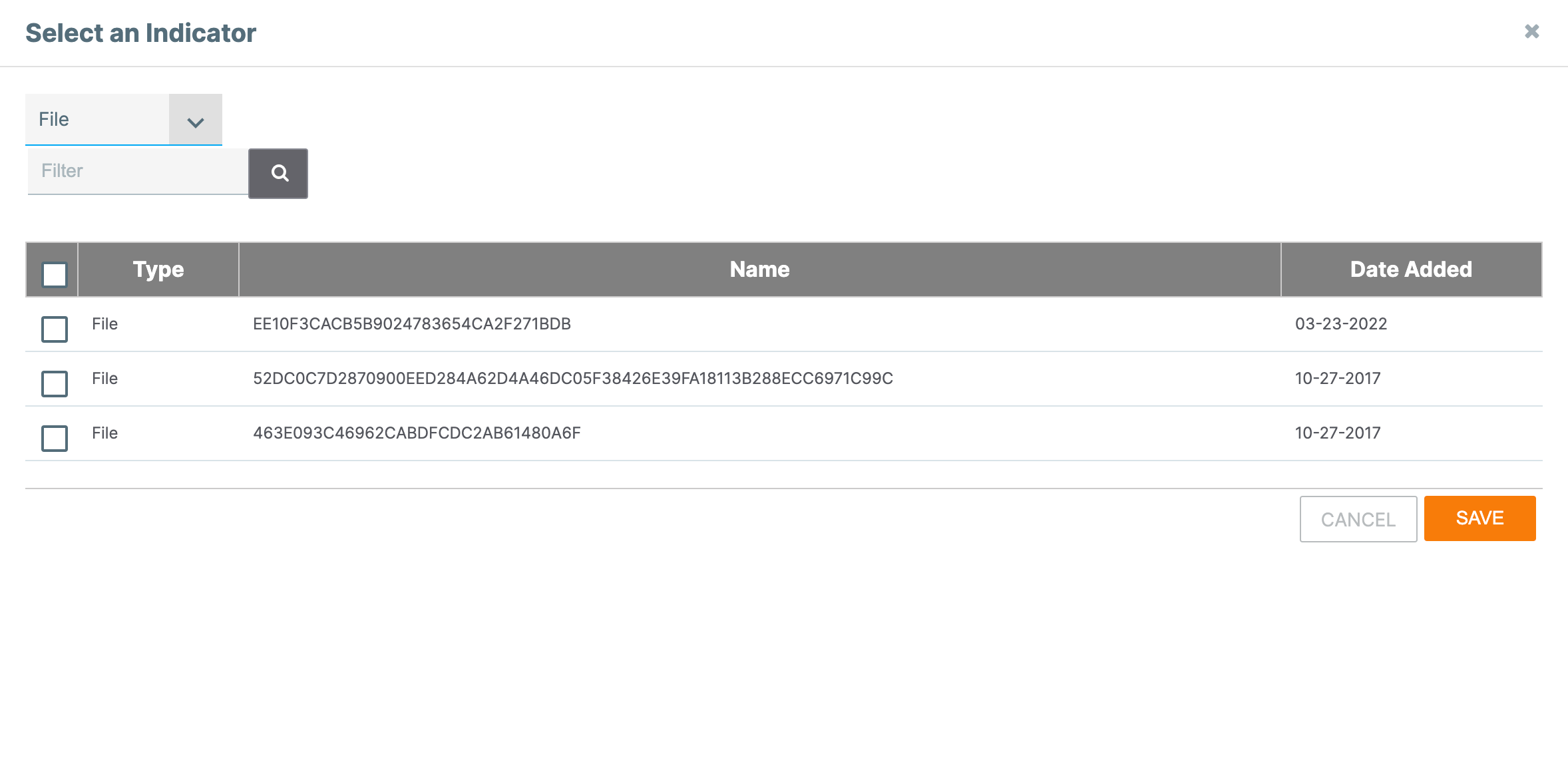
- Select one or more Indicators to associate to the primary File Indicator. If desired, use the Type selector and Filter box to filter Indicators by type and summary, respectively.
- Click the SAVE button.
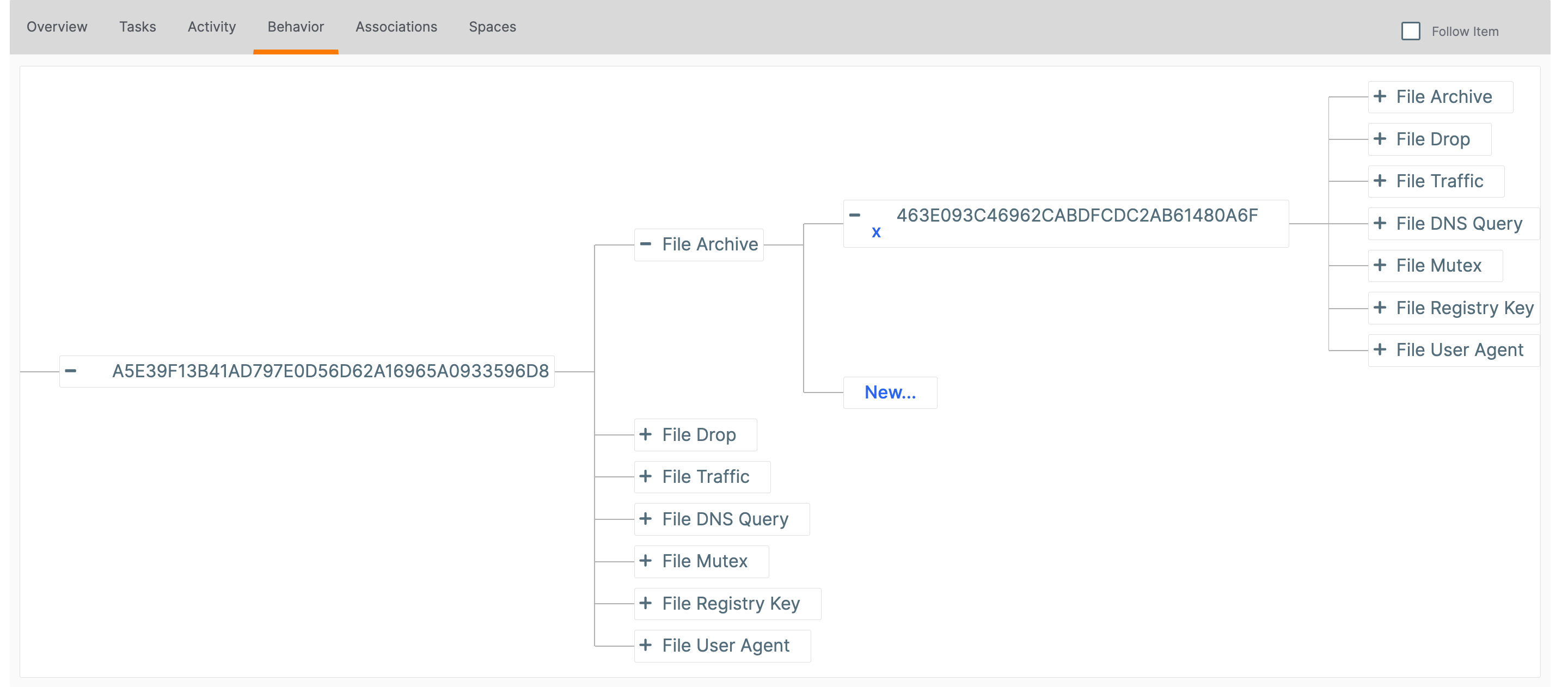
The new association will be displayed (Figure 4). Note that File behavior can be nested; that is, a dropped File Indicator can subsequently have its own behavior, which will be reflected in the model.
ThreatConnect® is a registered trademark of ThreatConnect, Inc.
20028-01 v.08.D
Was this article helpful?


