- 15 Mar 2023
- 4 Minutes to read
-
Print
-
DarkLight
Creating Indicator Exclusion Lists
- Updated on 15 Mar 2023
- 4 Minutes to read
-
Print
-
DarkLight
Overview
Indicator Exclusion Lists are created to prevent the import of Indicators that may be deemed legitimate or non-hostile to an organization. ThreatConnect® allows System Administrators to create Indicator Exclusion Lists at the System level and Organization Administrators to create Indicator Exclusion Lists at the Organization level. See ThreatConnect System Administration Guide for more information on System-level Indicator Exclusion Lists. This article covers Organization-level Indicator Exclusion Lists.
Table 1 displays a list of features and actions and specifies whether they are affected by an Indicator Exclusion List.
| Item | Yes | No |
|---|---|---|
| Manual Creation | ✔ | |
| Structured Import | ✔ | |
| Unstructured Import | ✔ | |
| E-mail Ingestion (Phishing and Feed) | ✔ | |
| Source Feed Monitor | ✔ | |
| STIX/TAXII Feeds | ✔ | |
| API Creation | ✔ | |
| API Bulk Import | ✔ | |
| Contribute/Copy to my Org | ✔ | |
| pDNS | ✔ | |
| Track Import | ✔ | |
| DNS Monitoring | ✔ |
Before You Start
| Minimum Role(s) | Organization role of Organization Administrator |
|---|---|
| Prerequisites | To add an Indicator to an Organization-level Exclusion List from the Indicator’s Details screen, a System Administrator must enable the system setting that allows this functionality, and you must be on a Dedicated Cloud instance of ThreatConnect |
Creating Indicator Exclusion Lists
- On the top navigation bar, hover the cursor over Settings
 and select Org Config. The Organization Config screen will be displayed with the Attribute Types tab selected.
and select Org Config. The Organization Config screen will be displayed with the Attribute Types tab selected. - Click the Indicator Exclusions tab. The Indicator Exclusions screen will be displayed (Figure 1).
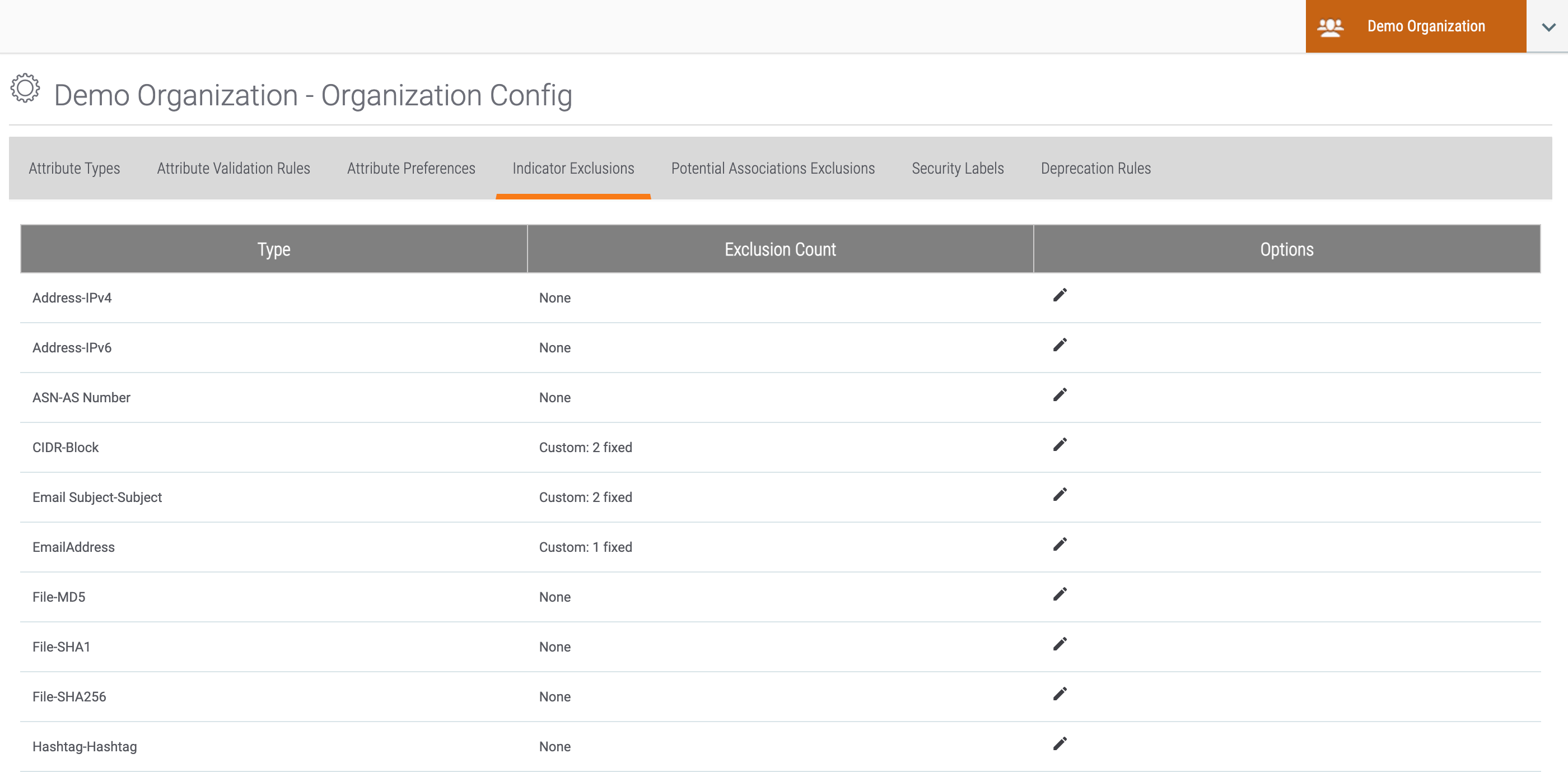
- Click Edit
 in the Options column for an Indicator (Host in this example). The Exclusion Details window for the selected Indicator type will be displayed (Figure 2).
in the Options column for an Indicator (Host in this example). The Exclusion Details window for the selected Indicator type will be displayed (Figure 2).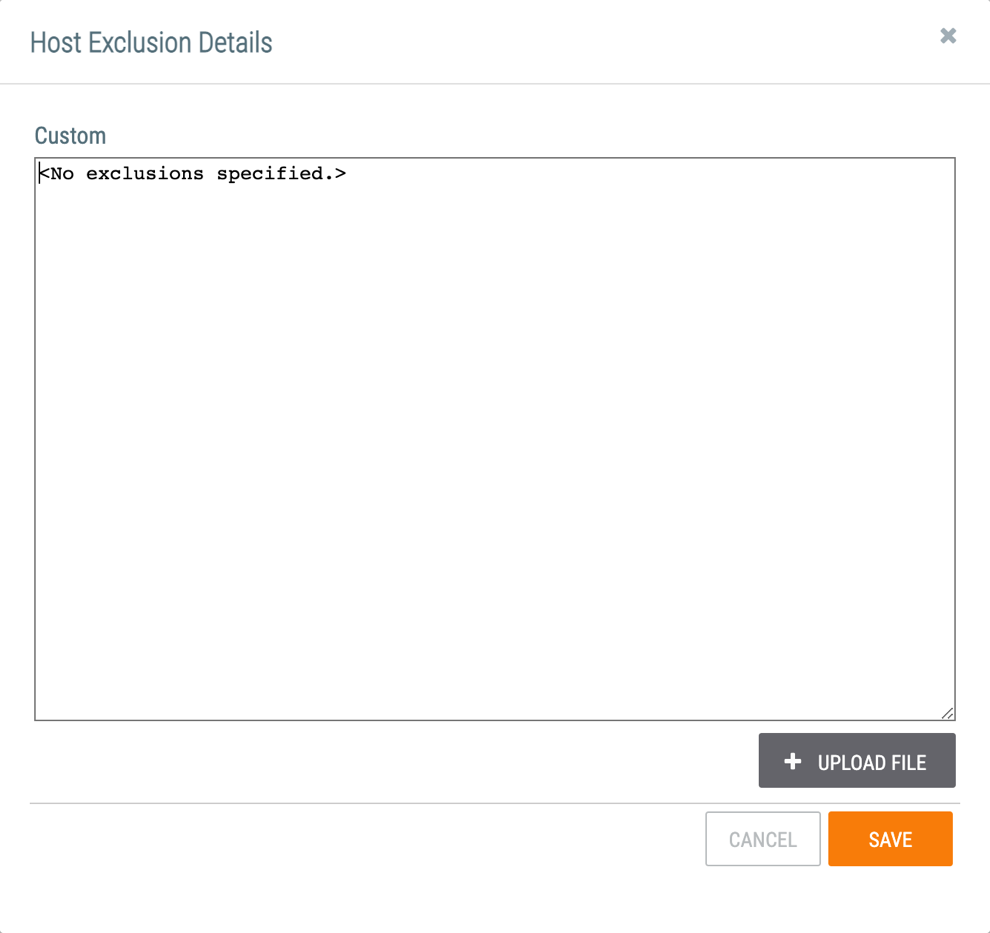
- Custom: Enter the Indicator(s) to be added to the Exclusion List in this text box.
- + UPLOAD FILE: Click this button to upload a .txt file containing the Indicator(s) to be added to the Exclusion List.NotePlace an asterisk (*) at the beginning and end of an Indicator to exclude all results. For example, entering *xyz.com* in the URL Exclusion List will exclude any URLs that contain the string xyz.com.NoteYou can enter additional Indicators into the Custom text box after uploading an Exclusion List file. However, if you enter Indicators into the Custom text box and then upload a file, the Indicators entered before the upload will be overwritten by the file’s contents.
- Click the SAVE button.
Clearing and Downloading Indicator Exclusion Lists
Follow Steps 1–3 in the “Creating Indicator Exclusion Lists” section to access the Exclusion Details window for an Indicator type. If an Exclusion List was previously created for an Indicator type, a DOWNLOAD button and a CLEAR button will be displayed (Figure 3).
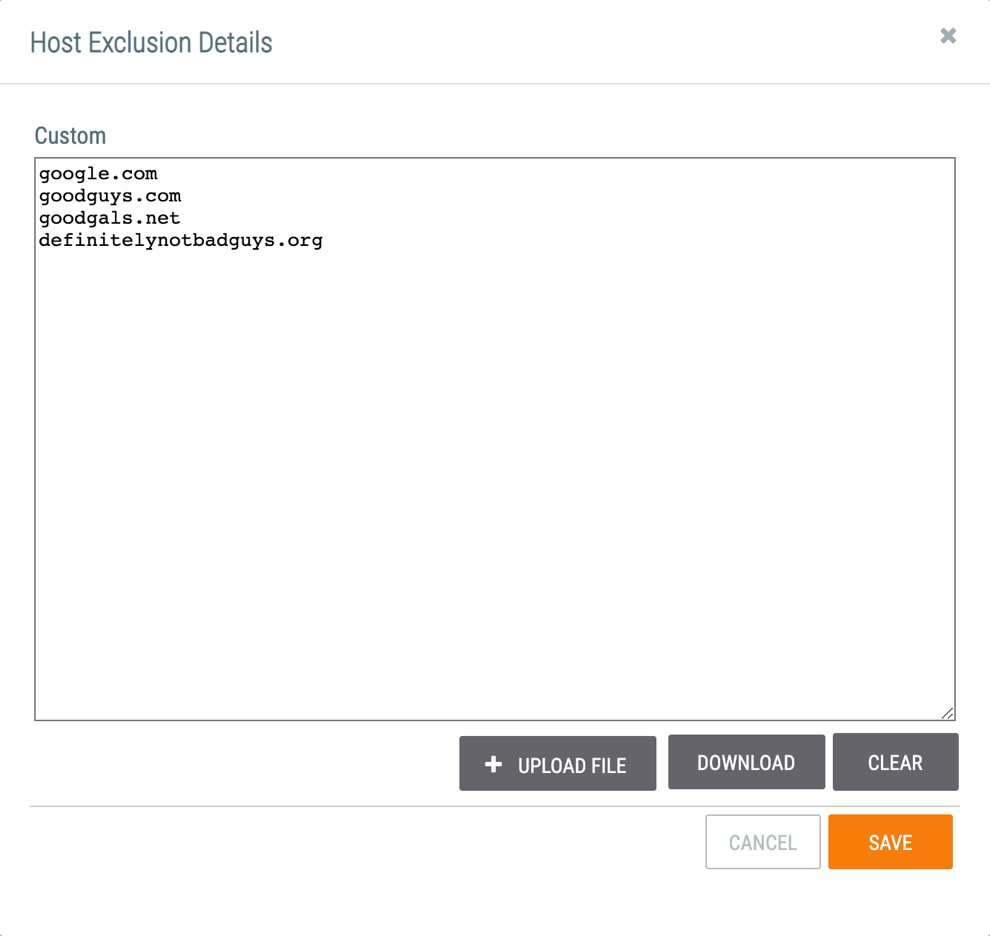
- CLEAR: Click this button to remove all Indicators from the Exclusion List.
- DOWNLOAD: Click this button to download the contents of the Exclusion List in a .txt file.
Adding an Indicator to an Exclusion List from the Details Screen
On Dedicated Cloud instances of ThreatConnect, Organization and System Administrators can add an Indicator to an Organization-level Exclusion List from the Indicator’s Details screen if a System Administrator has enabled this ability on their ThreatConnect instance.
New Details Screen
On an Indicator’s Details screen, click on the Options  button at the upper-right corner of the screen and select Add to Exclusion List to add the Indicator to the Exclusion List corresponding to its Indicator type (Figure 4). After you select this option, a message will be displayed at the lower-left corner of the screen confirming that the Indicator was added to the Exclusion List.
button at the upper-right corner of the screen and select Add to Exclusion List to add the Indicator to the Exclusion List corresponding to its Indicator type (Figure 4). After you select this option, a message will be displayed at the lower-left corner of the screen confirming that the Indicator was added to the Exclusion List.
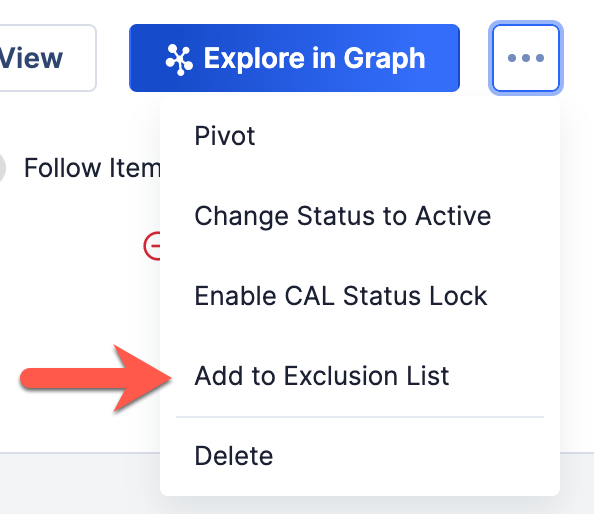
Legacy Details Screen
On an Indicator’s legacy Details screen, select the Add to Exclusion List checkbox displayed in the Indicator Status section to add the Indicator to the Exclusion List corresponding to its Indicator type (Figure 5). After you select this checkbox, a message will be displayed at the lower-left corner of the screen confirming that the Indicator was added to the Exclusion List.
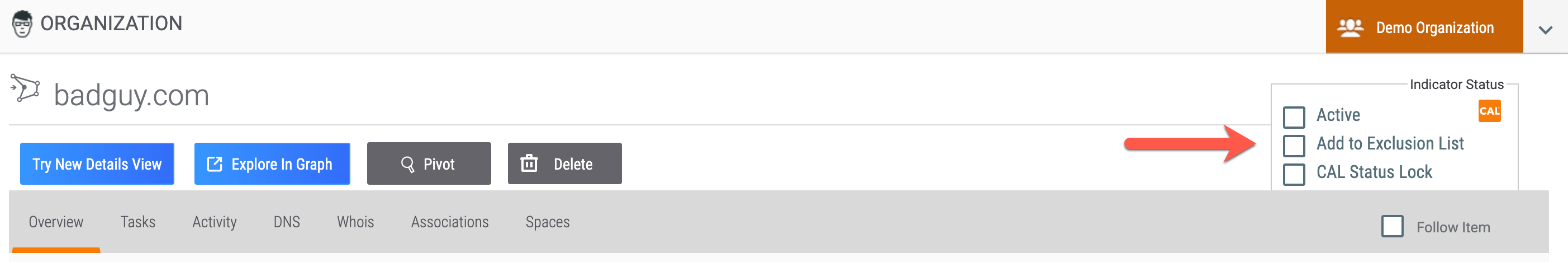
Removing an Indicator from an Exclusion List
Follow these steps to remove an Indicator from your Organization’s Exclusion List:
- Navigate to the Indicator Exclusions tab of the Organization Config screen (Figure 1).
- Click Edit
 for the Exclusion List corresponding to the Indicator’s type. The Exclusion Details window for that Indicator type will be displayed (Figure 3).
for the Exclusion List corresponding to the Indicator’s type. The Exclusion Details window for that Indicator type will be displayed (Figure 3). - Delete the Indicator’s entry in the Custom text box.
- Click the SAVE button.
ThreatConnect® is a registered trademark of ThreatConnect, Inc.
20046-01 v.09.A


