- 17 Jan 2024
- 11 Minutes to read
-
Print
-
DarkLight
The ThreatConnect Data Model
- Updated on 17 Jan 2024
- 11 Minutes to read
-
Print
-
DarkLight
Overview
ThreatConnect® models threat intelligence primarily in two categories: Indicators and Groups. Each category has some unique abilities and constraints that determine its behavior within ThreatConnect. In addition to Indicators and Groups, Intelligence Requirement objects model a collection of topics or a research question reflecting an organization’s cyber threat–related priorities that guides a security or threat intelligence team’s research and analysis efforts.
The Workflow feature in ThreatConnect allows you to combine manual and automated operations to define consistent and standardized processes for your security teams, including malware analysis, phishing triage, alert triage, intel requirement development, escalation procedures, and breach standard operating procedures. It is tied to the ThreatConnect data model through its use of Artifacts that map to ThreatConnect Indicator types.
Before You Start
| Minimum Role(s) | Organization role of Read Only User |
|---|---|
| Prerequisites | None |
Indicators
An Indicator represents an atomic piece of information that has some intelligence value, regardless of where it exists on ThreatConnect’s Diamond Model. Indicators are guaranteed to be unique within an owner. For example, a single Organization can have only one copy of the Email Address Indicator badguy@bad.com.
Indicator Types
Indicators are classified in 12 categories:
- Address: An Address Indicator represents a valid IP address, either IPv4 or IPv6
(e.g., 192.168.0.1). For IPv6, supported representations are standard (e.g., 1762:0:0:0:0:B03:1:AF18), “exploded” standard (e.g., 1762:0000:0000:0000:0000:0B03:0001:AF18), and compressed (e.g., 1762::B03:1:AF18). Mixed notation is not supported (e.g., 1762:0:0:0:0:B03:127.32.67.15). - ASN: An ASN (Autonomous System Number) Indicator represents a number that uniquely identifies each network on the Internet (e.g., ASN204288).
- CIDR: A CIDR (Classless Inter-Domain Routing) Indicator represents a block of network IP addresses (e.g., 10.10.1.16/32).
- Email Address: An Email Address Indicator represents a valid email address
(e.g., badguy@bad.com). - Email Subject: An Email Subject Indicator represents the subject line of an email.
- File: A File Indicator represents a unique file hash or series of hashes. Supported hashes are MD5, SHA-1, and SHA-256.
- Hashtag: A Hashtag Indicator represents a hashtag term as used in social media.
- Host: A Host Indicator represents a valid hostname, which is also referred to as a domain (e.g., bad.com).
- Mutex: A Mutex Indicator is a synchronization primitive that can be used to identify malware files and relate malware families (e.g., \Sessions\1\BaseNamedObjects\Globa\CLR_PerfMon_WrapMutex).
- Registry Key: A Registry Key Indicator represents a node in a hierarchical database that contains data critical for the operation of Windows and the applications and services that run on Windows (e.g., HKEY_CURRENT_USER\Software\MyApp).
- URL: A URL Indicator represents a valid URL, including protocol
(e.g., http://www.bad.com/index.php?id=1). URLs are accepted according to RFC 3986, with a few exceptions: Underscore (_) is an allowed character for the third label (i.e., subdomains); the host section of the authority part must be lowercase; URL encoding is not verified (% is simply an accepted character in the path, query, and fragment); and user information must be removed from the authority part. Accepted schemes are http, https, ftp, and sftp. The host section of the authority part can be a hostname or an IPv4 address. - User Agent: A User Agent Indicator is a characteristic identification string that a software agent uses when operating in a network protocol [e.g., Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_2) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/55.0.2883.95, Safari/537.36].
Viewing Indicators
On the top navigation bar, hover over Browse and select Indicators or an Indicator type (e.g., Host) to display a results table containing all Indicators or all Indicators of that type, respectively, on the Browse screen.
To view more information on a particular Indicator, navigate to its Details screen. The Overview tab of an Indicator’s Details screen contains cards displaying information about the Indicator, including data specific to that Indicator type. For example, the Details screen for a File allows you to edit a file’s hashes and size, and the Details screen for an Address displays IP geolocation data. An Indicator’s Details screen also includes tabs providing information on the Indicator’s associations, user activity involving the Indicator, and enrichment services available for the Indicator’s type.
Groups
Groups represent a collection of related behavior and intelligence.
Group Types
Groups are classified in 17 categories. Definitions for Attack Pattern, Course of Action, Malware, Tactic, Tool, and Vulnerability Group types are aligned with STIX™ 2.1 definitions for STIX Domain Objects.
- Adversary: The Adversary Group represents a malicious actor. An Adversary can be tracked by its assets (e.g., websites, email addresses, hacker handles, etc.) to allow for monitoring of activity.
- Attack Pattern: The Attack Pattern Group represents a type of tactics, techniques, and procedures (TTP) that describes ways that adversaries attempt to compromise targets.
- Campaign: The Campaign Group represents a collection of Incidents over time. (See “Incident” later in this list.)
- Course of Action: The Course of Action Group represents a recommendation from a producer of intelligence to a consumer on the actions that they might take in response to that intelligence.
- Document: The Document Group represents a file of interest, such as a PDF report that contains valuable intelligence or a malware sample. Documents can have their contents indexed for future searching.
- E-mail: The E-mail Group represents an occurrence of a specific suspicious email, such as a phishing attempt.
- Event: The Event Group is an observable occurrence of notable activity in an information system or network that may indicate a security incident. For example, an Event might be created from a SIEM alert that needs to be triaged and investigated.
- Incident: The Incident Group represents a snapshot of a particular intrusion, breach, or other event of interest.
- Intrusion Set: The Intrusion Set Group is a set of adversarial behaviors and resources with common properties that is believed to be orchestrated by a single organization. An Intrusion Set may capture multiple Campaigns or other activities that are all tied together by shared attributes indicating a common known or unknown Adversary. New activity can be attributed to an Intrusion Set even if the Adversaries behind the attack are not known. Adversaries can move from supporting one Intrusion Set to supporting another, or they may support multiple Intrusion Sets.
- Malware: The Malware Group is a type of TTP that represents malicious code.
- Report: The Report Group is a generic object that can hold a collection of threat intelligence focused on one or more topics, such as a description of a threat actor, malware, or attack technique, including context and related details. It can be used to group related pieces of threat intelligence together so that they can be published as a comprehensive cyberthreat story. Reports can be used to memorialize and distribute a wide variety of threat reports, such as reports on malware families, risk reports on specific infrastructure, and even writeups on physical security. PDF and HTML files uploaded to a Report are viewable directly on the Report File card on the Overview tab of that Report’s Details screen. The Report Group is designed to be a neutral object that is suitable for a variety of topics. This design is in contrast to that of other Groups such as Adversary and Incident, which have more specific definitions.ImportantThe Report Group object is a separate entity from the reports that you can create via the Reporting option on the top navigation bar in ThreatConnect.
- Signature: The Signature Group represents an actual Signature that can be used for detection or prevention in a supported format (i.e., Bro, ClamAV®, CybOX™, Iris® Search Hash, Microsoft® Kusto Query Language [KQL], OpenIOC, Regex, Splunk® Search Processing Language (SPL), Sigma, Snort®, STIX™ Pattern, Suricata, ThreatConnect Query Language (TQL) Query, and YARA).NoteSystem Administrators may create custom Signature types.
- Tactic: The Tactic Group represents an action or strategy carefully planned to achieve a specific end.
- Task: The Task Group represents an assignment given to a ThreatConnect user.
- Threat: The Threat Group represents a group of related activity, whether or not attribution is known. This relation can be based on technology (e.g., Shellshock) or pertain to a grouping of activity that is presumed to be by the same selection of actors (e.g., Bitterbug).
- Tool: The Tool Group represents legitimate software that can be used by threat actors to perform attacks.
- Vulnerability: The Vulnerability Group represents a mistake in software that can be directly used by a hacker to gain access to a system or network.
Viewing Groups
On the top navigation bar, hover over Browse and select Groups or a Group type (e.g., Adversary) to display a results table containing all Groups or all Groups of that type, respectively, on the Browse screen.
To view more information on a particular Group, navigate to its Details screen. The Overview tab of a Group’s Details screen contains cards displaying information about the Group, such as Security Labels and Attributes. A Group’s Details screen also includes tabs providing information on the Group’s associations and user activity involving the Group.
Intelligence Requirements
Intelligence Requirements (IRs) represent a collection of topics or a research question reflecting an organization’s cyber threat–related priorities that guides a security or threat intelligence team’s research and analysis efforts.
Intelligence Requirement Subtypes
IRs are classified in five subtypes:
- Intelligence Requirement (IR): This subtype represents threats of overall concern to an organization (e.g., cyber threats, fraud, geopolitical/physical threats).
- Priority Intelligence Requirement (PIR): This subtype represents threat actor motives; tactics, techniques, and procedures (TTPs); targets; impacts; or attributions in association with IRs.
- Specific Intelligence Requirement (SIR): This subtype represents facts associated with threat activity, such as indicators of compromise (IOCs).
- Request for Information (RFI): This subtype represents one-off requests for information related to topics of interest to particular stakeholders.
- Research Requirement (RR): This subtype represents a topic or area of investigation that is of interest to an individual or group and does not merit a full intelligence requirement, but does require tracking of relevant information.
Viewing Intelligence Requirements
On the top navigation bar, hover over Browse and select Intelligence Requirements (IR) to display a results table containing all IRs in your Organization on the Browse screen.
To view more information on a particular IR, navigate to its Details screen. The Overview tab of an IR’s Details screen contains cards displaying information about the IR, including its subtype, category, keyword query, and results returned from its keyword query. An IR’s Details screen also includes a tab that provides information on the IR’s associations.
Associations
The functionality of associations allows you to model and discover correlations and relationships that may not have been immediately obvious. With this feature, you can
- associate Groups to IRs, Indicators, Victim Assets, and other Groups;
- associate Indicators to IRs, Groups, Victim Assets, and, using custom associations, other Indicators; and
- associate IRs to Indicators, Groups, and Victim Assets.
In addition, you can associate Groups, Indicators, and IRs to Workflow Cases and their Artifacts.
Figure 1 shows an example of the ThreatConnect data model, displaying the associations between different Groups (Adversary, Campaign, Incident, Signature, and Threat) and Indicators (IP Address, Email Address, File, and Host). Following the diagram is an explanation of the associations.
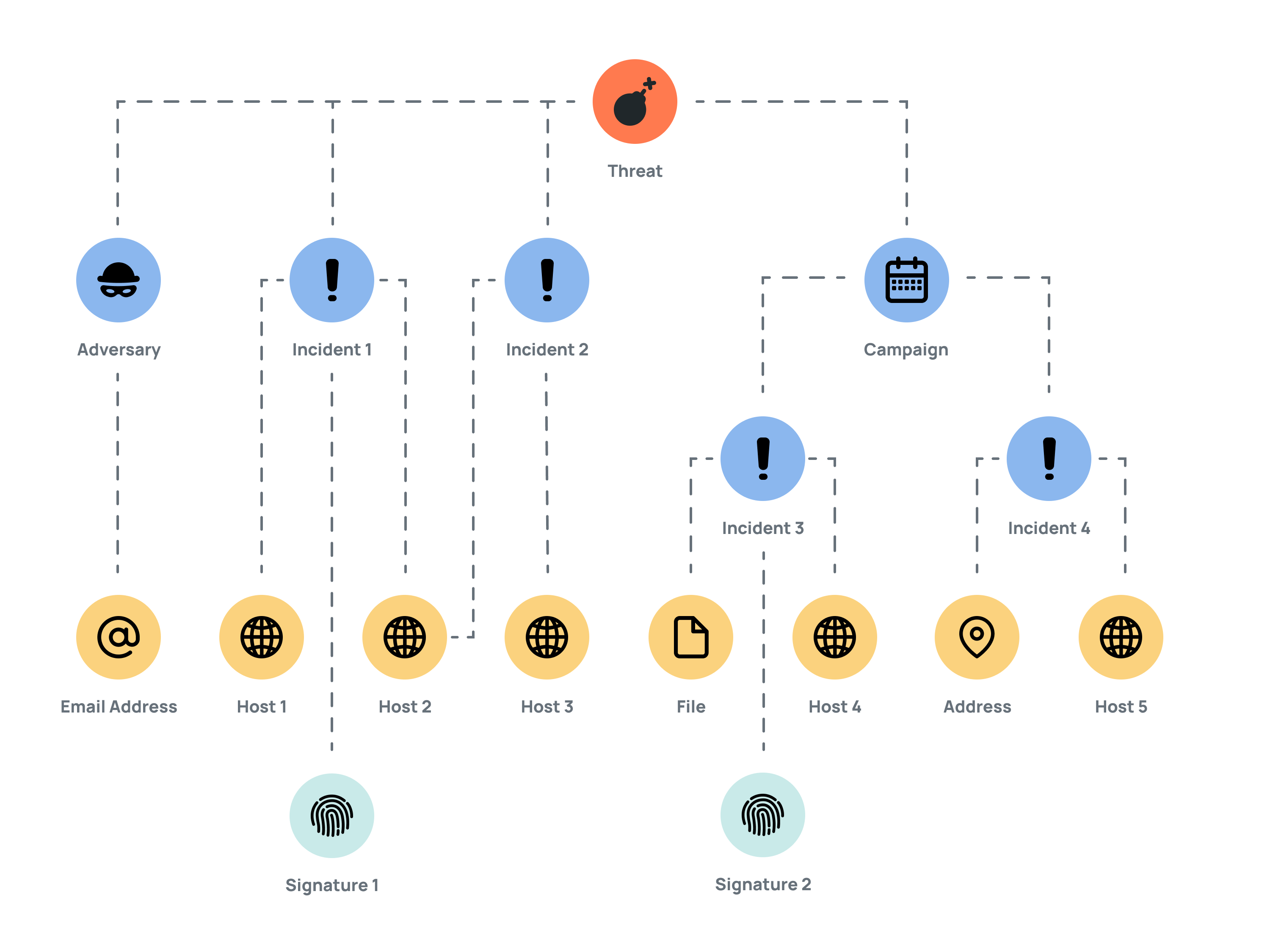
A Threat, which is identified as an overseas hacking unit, is associated with the following objects:
- Adversary: This object is a malicious actor with ties to other malicious actors. Its Email Address is listed as the Start of Authority (SOA) record for domains used by the Threat.
- Incident1: A domain, and the internet provider that hosted it, was identified in open-source reporting in a cybersecurity-industry blog detailing the Threat's activity. Host 1 and Host 2 have been previously used by the Threat's infrastructure and are associated with Incident 1. Snort Signature1, used to detect network Indicators, is associated with Host 1 and Host 2 through their rules.
- Incident2: The cybersecurity-industry blog also identified a new series of phishing attacks from the Threat, targeting foreign journalists, politicians, and activists. These attacks are focused on stealing email-account details of the victims and finding information about their contacts and networks. Host 2 and Host 3, identified as having been used by the Threat's infrastructure, are associated with Incident 2.
- Campaign: This effort targets foreign organizations involved in the technology, government, and energy sectors. It is directly tied to the Threat. Through Incident 3, ThreatConnect identified a malicious File that is likely the Campaign's malware, which, when executed, connects to Host 4. Snort Signature 2, which is used to detect network Indicators, is associated with Incident 3, and the Snort rules connect to the rules of Host 4. In Incident 4, over fifty samples of the tools used by the Campaign were collected. These tools included IRC bots, an open-source Python remote-access tool, malicious macros, and others. The Campaign uses the IP Address as its command-and-control IP address and Host 5 as its command-and-control domain.
Workflow and Case Management
Workflow in ThreatConnect supports the concept of case management, which gives you the capability to investigate and track information security threats and incidents by
- minimizing the time it takes to match a case to historical data;
- minimizing the time it takes to assess scope;
- minimizing the time it takes to assess impact; and
- maximizing the amount of information that can be turned into actionable intelligence for later use.
In Workflow Cases, Artifacts are pieces of data that provide information to a Case that may be useful to an analyst. You can add Artifacts that map to ThreatConnect Indicator types to your Organization. Additional information on the Indicator may be available if the Indicator already exists on your ThreatConnect instance. It is the Artifact component within Workflow that ties Workflow to the ThreatConnect data model.
See Workflow Overview for more information on Workflow in ThreatConnect, including definitions of key terms, process flow, and links to articles that provide further details on Workflow Playbooks, Workflows and Workflow Templates, Cases, and Tasks.
ThreatConnect® is a registered trademark of ThreatConnect, Inc.
ClamAV® and Snort® are registered trademarks of Cisco Systems, Inc.
CybOX™ and STIX™ are trademarks of The MITRE Corporation.
Iris® is a registered trademark of DomainTools, LLC.
Microsoft® is a registered trademark of Microsoft Corporation.
Splunk® is a registered trademark of Splunk, Inc.
20027-01 v.16.B


